The default iptables configuration on CentOS or RHEL does not allow access to the HTTP (TCP PORT # 80) and HTTPS (TCP PORT # 443) ports used by the Apache web server. You can modify settings using any one of the following three methods:
- /etc/sysconfig/iptables : Edit this file to allow or deny access to the Apache Web Server IPv4. You also need to edit the /etc/sysconfig/ip6tables file to allow or deny access to the Apache Web Server IPv6 ports.
- system-config-firewall-tui command (runs on ssh text based session) or system-config-firewall command (run on GUI based session) : This is a graphical user interface for setting basic firewall rules. This tool will always overwrite /etc/sysconfig/iptables file.
- /sbin/iptables command : Use iptables command directly to modify/append/add firewall rules. The rules can be saved to /etc/sysconfig/iptables file with /sbin/service iptables save command.
Method # 1: Edit /etc/sysconfig/iptables file (recommend for advanced users)
Edit the IPv4 /etc/sysconfig/iptables, enter:# vi /etc/sysconfig/iptables
Add the following lines, ensuring that they appear before the final LOG and DROP lines for INPUT chain:
## allow everyone to access port 80 and 443 (IPv4 Only)## -A INPUT -m state --state NEW -p tcp --dport 80 -j ACCEPT -A INPUT -m state --state NEW -p tcp --dport 443 -j ACCEPT
Save and close the file. Restart the IPv4 iptables service:# service iptables start
Edit the IPv6 /etc/sysconfig/ip6tables, enter:# vi /etc/sysconfig/ip6tables
Add the following lines, ensuring that they appear before the final LOG and DROP lines for INPUT chain:
## allow everyone to access port 80 and 443 (IPv6 Only)## -A INPUT -m state --state NEW -m tcp -p tcp --dport 80 -j ACCEPT -A INPUT -m state --state NEW -m tcp -p tcp --dport 443 -j ACCEPT
Save and close the file. Restart the IPv6 iptables service:# service ip6tables restart
Method # 2: Firewall configuration GUI/TUI tool (recommend for new users)
The
system-config-firewall command is a graphical user interface for
setting basic firewall rules. You need to have KDE or Gnome installed on
the system. Open a terminal and type the following command as root
user:# system-config-firewall
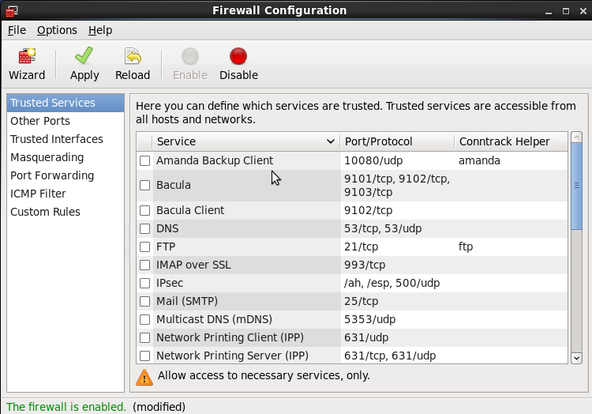
Sample outputs:
Fig.01: GUI tool in action
Select services such as WWW, SSH, HTTPS to open port for everyone.
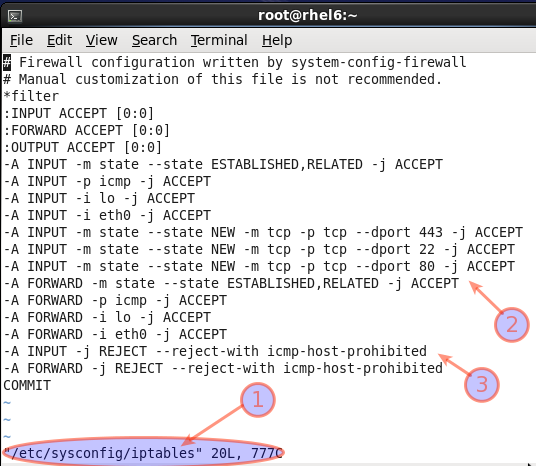
Click on Apply button. This tool will generate /etc/sysconfig/iptables
as follows:
Sample RHEL CentOS Linux /etc/sysconfig/iptables files
A note about text based config tool (recommend for remote server with ssh access)
The sysystem-config-firewall-tui is a command line tool without having the GUI installed on the server:# system-config-firewall-tui
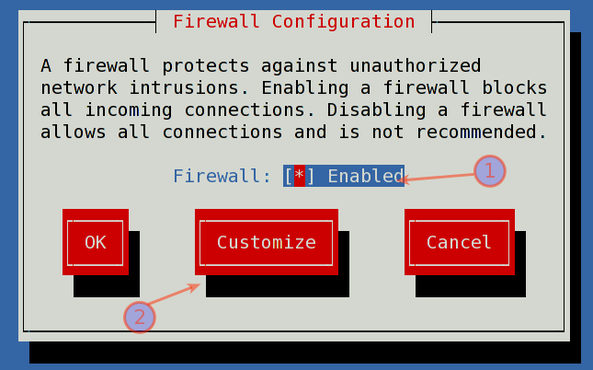
Sample outputs:
Fig.02: system-config-firewall-tui in action
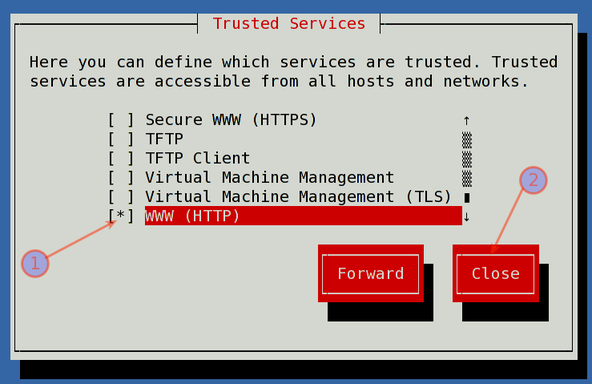
Select Enabled and Press Tab to select "Customization" :
Fig.03: Opening a port 80
Scroll down/up and select SSH, WWW, Secure WWW (HTTPS) and other required ports you wish to open. Finally, select Close button. Finally, press OK button to activate new firewall settings.
Method # 3: /sbin/iptables command line utility (recommend for advanced/expert users only)
Type the following iptables command as root user to open port 80 / 443:
## open port 80 and 443 for everyone ## /sbin/iptables -A INPUT -m state --state NEW -p tcp --dport 80 -j ACCEPT /sbin/iptables -A INPUT -m state --state NEW -p tcp --dport 443 -j ACCEPT ## save newly added firewall rules ## /sbin/service iptables save ## verify new firewall settings /sbin/iptables -L -n -v /sbin/iptables -L INPUT -n -v /sbin/iptables -L INPUT -n -v | grep :80 /sbin/iptables -L INPUT -n -v | grep :443
The following rule allows access to port 80 and 443 only to 192.168.1.0/24
## Find an appropriate network block, and network mask ## representing the machines on your network which should operate as ## clients of the Apache Web-server ## Open port 80 and 443 for 192.168.1.0/24 subnet only ## /sbin/iptables -A INPUT -s 192.168.1.0/24 -m state --state NEW -p tcp --dport 80 -j ACCEPT /sbin/iptables -A INPUT -s 192.168.1.0/24 -m state --state NEW -p tcp --dport 443 -j ACCEPT ## save newly added firewall rules ## /sbin/service iptables save ## verify new firewall settings /sbin/iptables -L -n -v /sbin/iptables -L INPUT -n -v /sbin/iptables -L INPUT -n -v | grep :80 /sbin/iptables -L INPUT -n -v | grep :443
You can block/drop the IP address 202.54.1.1 or subnet 202.54.1.2/29 as follows using iptables:
## Block access to port 80 ## iptables -A INPUT -s 202.54.1.1 -p tcp --dport 80 -j DROP iptables -A INPUT -s 202.54.1.2/29 -p tcp --dport 80 -j DROP ## block and drop access to port 443 (secure apache web-server) iptables -A INPUT -s 202.54.1.1 -p tcp --dport 443 -j DROP iptables -A INPUT -s 202.54.1.2/29 -p tcp --dport 443 -j DROP ## save newly added firewall rules ## /sbin/service iptables save ## verify new firewall settings /sbin/iptables -L -n -v /sbin/iptables -L INPUT -n -v | grep 202.54.1.1
Note: To unblock an IP i.e. delete the IP address 202.54.1.1 listed in iptables type the following command:iptables -D INPUT -s 202.54.1.1 -j DROP